Crypto data fishing fraud will cost users in April $ 5.29 million when attack tactics diversify
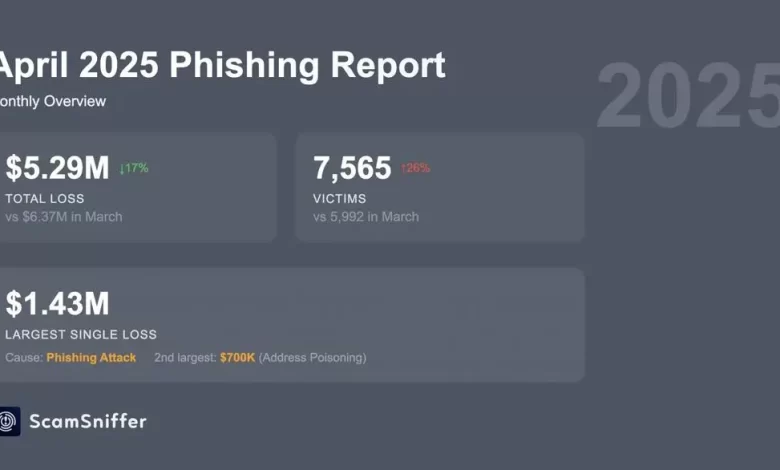
According to Scamsniffer's latest report, crypto users lost $ 5.29 million to data fishing fraud in April 2025. The Spile reporting platform noted that this means a 17% decline compared to the loss of March.
However, the number of victims of data fishing increased significantly AprilA total of 7565 addresses affected by attacks. This is a 26% growth compared to 5992 victims in March and highlights the evolving tactics of fraudsters.
The biggest loss of the month was $ 1.43 million, the whale lost due to the signing of several data fishing. This shows that high -value victims remain vulnerable, as the biggest attack in March was Vaal, which lost $ 1.82 million to a similar attack vector.

There were other users who lost significant amounts to signed data signatures. These include the user's 0xC1E4260cb, which lost $ 666,414 and 0x7c930969fcf, who lost $ 234,000.
In the meantime, last month the second largest attack was $ 700,000 by one user copying the wrong address. Address poisoning has been one of the main reasons for the loss of data fishing this year and it seems to continue.
In this case, the victim copied the fake address, which shared the same first six character at the legitimate address, while the last four characters were the same except in different alphabet cases.
Not surprisingly, there were other significant losses due to address poisoning. In one case, the other user lost $ 150,000 because they copied the wrong address while the 0xefc4f1D5 also sent $ 467,175 to the wrong address for the same reason.
However, April is the loss of the lowest cryptocurrency of the month, except for February, which was $ 5.32 million.
Cheaters are planning new ways to attack users
In the meantime, in April, fraudsters also saw a variety of tools to target users. Fellow Detected fake Solscan ads in Google search results as data fishing links, noting that the ham site was a leading search result on Google when the user searched for Solscan.
This noted:
“These data fishing ads are designed to empty your wallet through the signatures of a malicious transaction.”
While the URL of the data fishing link and the authentic page appear to be the same, clicking on the link is actually directing users to solscan.com. Google has removed the ad.
Interestingly, fake Google ads were not the only tools through which the attackers use users. Nick Johnson, the developer of Ethereum's name service, also identified another e -mail data fishing attack aimed at Google's accounts, fraudsters introducing fake login pages using Google Sites to ensure credibility.
As fraudsters are based on different techniques for crypto users, security analysts continue to emphasize how people can protect themselves from such attacks by identifying when they are in Phater.
Scamsniffer shared infographic On this page, which shows a variety of ways for fraudsters to start these attacks using Twitter, Discord, Airdrop, scams and software compromises. All popular data fishing signatures were also identified, which users can unknowingly sign and lose their property.
In the meantime Withdraw cash Having posted the necessary precautions to prevent address poisoning. These precautions include double verification of all addresses before making a transaction, not copying from transaction history and using bookmarks or white lists of white lists.
364 million dollars lost to Crypto Hacks in April
Meanwhile, more than $ 5 million in data fraud is only a small percentage of cryptocurrencies in April. According to the Blockchain security company CeriaA total of $ 364 million disappeared in April for hacks and fraud.
One case was responsible for the loss for $ 336 million, which included an attack on social engineering, resulting in a 3,520 bitcoin theft from one person who had been asset since 2017. The Sleuth Zachxbt chain confirmed that the victim was an elderly person in the United States.

Certik categorized this attack as data fishing. With these metrics, the loss of what had happened together meant $ 1.36 million lost in the $ 1.36 million poisoning that the data category had a total loss of $ 337 million in April.
In addition to this attack, hackers also used a decentralized exchange of exchange koloex for $ 7.5 million, dragged $ 5.8 million from Loopscale and stole $ 5.5 million from the ZKSync Airdrop contract. Bitcoin mission and terms also lost $ 2 million and $ 1.57 million respectively.
Cryptopolitan Academy: Soon – a new way to earn a passive income with a defi in 2025. For more information




